 I’m often asked by friends and family who have old computers that they want to dispose of, give away or sell, how to securely wipe a Hard Disk Drive.
I’m often asked by friends and family who have old computers that they want to dispose of, give away or sell, how to securely wipe a Hard Disk Drive.
Used Hard Disk Drives on eBay are often ripe with leftover data, leaving the former owner of the computer open to identity theft or other nefarious challenges.
Wiping the data on a Hard Disk is therefore key before you sell, give away or even throw out an old computer.
Thankfully, there’s a simple solution.
Active KillDisk – Hard Drive Eraser
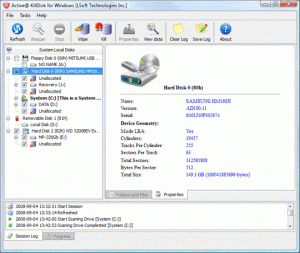 The software Active KillDisk is a free and easy to use tool that will help you securely wipe your Hard Disk drives before disposing of them.
The software Active KillDisk is a free and easy to use tool that will help you securely wipe your Hard Disk drives before disposing of them.
The KillDisk Freeware suite will help you create a Bootable USB Disk that you can then pop in the machine you want to wipe. Reboot with the USB Disk inserted, follow the instructions, and voila – your old HDD is wiped to a level that most eBay buyers or donation receivers will never be able to recover data from.
KillDisk also produces more advanced solutions for both Home and Business users, but for most friends and family, KillDisk Freeware should be sufficient.
Why Not Physically Destroy the Hard Disk?

I’ve heard the assumption that sticking a nail through the Hard Disk will also secure your data. With my green hat on, this isn’t a preferred option.
However, even if you couldn’t care less about the environmental impact of chucking out a dead hard disk, then be aware that I’ve seen experts demonstrate how they can recover data from even the most hammered Hard Disk Drives. For instance, I’ve attended a demonstration where the chaps over at Vogon Computer Forensics, who specialise in Computer Forensics and Data Recovery, will tell you stories about how they’ve recovered data from all sorts of situations where you’d have thought the HDD is unrecoverable.
[tweet_box design=”default”]Taking a hammer to your old hard disk drive is not enough – data can be recovered from even the most damaged hard disk[/tweet_box]
I also have friends who work in IT for UK Police Forces who tell me that when an HDD in one of their PC’s fails, even though it is swapped for a new model under Warranty, they destroy the data on the HDD before returning it to the manufacturer to err on the safe side.
Conclusion
The data stored on your Hard Disk Drives can easily be used to inflict identity theft, or worse, upon you.
Whenever you are selling, giving away or even throwing away an old computer, always make sure to use a tool such as Active KillDisk to securely wipe the data on your Hard Drive — formatting the disk is simply not effective enough.
[tweet_box design=”default”]If you’re selling, donating or throwing away an old computer, always use a tool such as Active KillDisk to securely wipe the data[/tweet_box]
You Might Also Be Interested In
How To Protect The Data On Your Laptop Computer
How To Choose The Correct Hard Disk Drive For Your Server or NAS












Comments