How many organisations have you shared your email address with over the years? Hundreds? Thousands? Have you ever wondered whether any of those organisations have been involved in a data breach?
Every Friday I share one of my favourite finds of the week — a website, tool or an app that has impressed me.
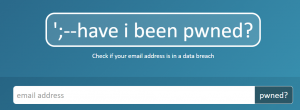
My Friday Favourite this week is Have I Been Pwned – Check if Your Email Address is in a Data Breach.
What is it?
Have I Been Pwned is a service that allows anyone to quickly assess if they may have been put at risk due to an online account of theirs having been compromised or “pwned” in a data breach.
How much does it cost?
The Have I Been Pwned service is free to use.
Check if Your Email Address is in a Data Breach
I’ve written extensively about Cyber Security for Small Businesses, and the importance of keeping clients data secure.
However, data breaches can and do happen. But how do you know if your data has been breached?
Have I Been Pwned is a web-site created by Microsoft Regional Director and web security evangelist Troy Hunt.
Hunt put together the site after what was, at the time, the largest ever single breach of customer accounts — the Adobe hack.
After the Adobe hack, Hunt said he did a post-breach analysis of user credentials and kept finding the same accounts exposed over and over again, often with the same passwords. This then put the victims at further risk of their other accounts being compromised.
(There’s a big lesson there about using a strong password and making sure you use different passwords for different web-sites).
That’s where Have I Been Pwned can help.
Simply visit the web-site, and enter your email address.
Immediately, you will be told whether your email address was involved in a data breach and which breach(es) it was involved in.
If you have not already changed your password for the sites that you find have been breached, then now is the time to do so!
You can also freely subscribe to get notified when future pwnage occurs and your account is compromised.
Have I Been Pwned will send you an email as and when it discovers new breaches that your email address has been involved in.
I talked to Kevin Lancaster of ID Agent about The Dark Web and Keeping Managed Service Provider (MSP) Clients Safe, and it’s truly terrifying to understand the market there is amongst cyber criminals for our personal data.
I’d recommend using Have I Been Pwned to stay aware of how data breaches can affect you.
How can I get it?
To find out more visit the Have I Been Pwned web-site.
You can also follow @TroyHunt (the creator of Have I Been Pwned) on Twitter, visit Troy Hunt’s Facebook page or follow Troy Hunt on LinkedIn.











Comments