The Pax8 Cybersecurity Masterclass is a great hands-on event for managed service providers (MSPs) to understand the risks in today’s threat landscape.
The topics explored in this one day event are aimed at helping IT providers develop a more comprehensive security stack.
They are hugely popular and are open to any MSP who is a Pax8 customer. Though to keep them intimate and more interactive, there are limited places available, and the classes are held once each month.
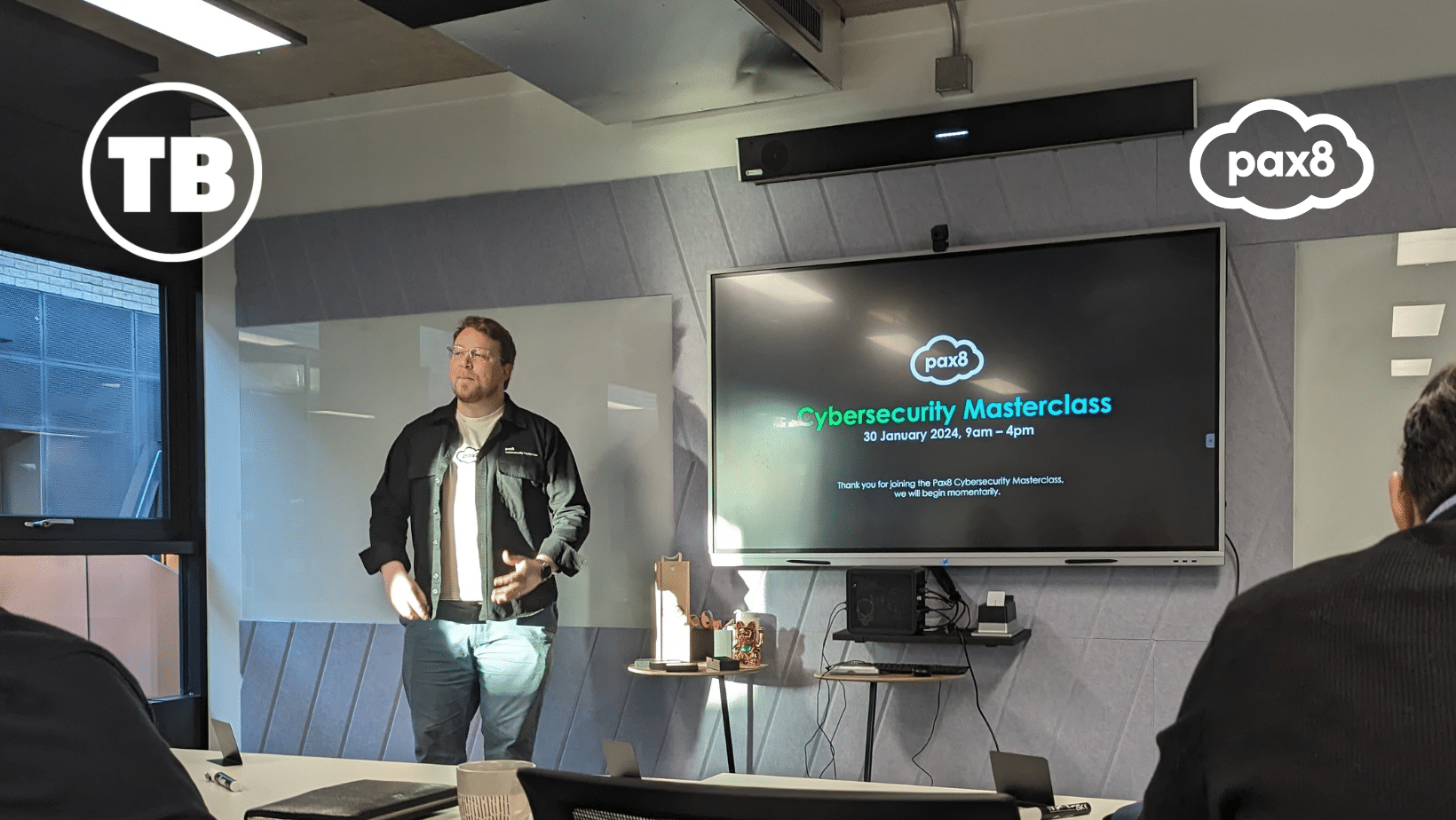
For the first Masterclass of 2024, I, Stephen McCormick, went along to see what they were all about.
Masterclass Introductions
Pax8’s Cybersecurity Masterclasses are held all across Europe.
The UK’s January Masterclass took place at Pax8’s offices in Bristol. Starting off with breakfast, and a chance to meet the other delegates.
Following on from that, we were ushered into the briefing room for introductions and housekeeping before the Masterclass began.
Alex Cotterell, Regional Sales Manager for Pax8 UK, started with a conversation, asking if anyone in the room would like to share their recent cybersecurity journey?
And from the responses, it was clear that MSPs had already got to grips with cybersecurity audits for their customers, but were here to gain more knowledge and confidence about best practice and selling solutions to customers.
The MSP Mindset
When it comes to your typical managed service provider they tend to fit a certain profile.
- MSPs are mostly male, middle class and aged between 35 and 55
- They’re more technically-focused, but usually time poor
- And analytical with an attention to detail and with tactical problem-solving tendencies
However, it’s important to remember that typical MSP customers are not like this!
So when communicating with customers, we have to consider what it is that matters to them.
How Clean is Your House?
Mostyn Thomas talked about the importance of depth of defence in cybersecurity and why we should experience what it’s like to protect our own business before securing those of our customers.
The Parallels with Casinos
Casinos have always taken a multi-layered approach when it comes to securing their money. Everyone in the casino’s employ are trained to keep a watchful eye on the players, and each other, in case someone attempts to cheat or steal from the business.
Now that casinos are online, they have some of the best security that money can buy, but even they can become victims of cyber criminals.
Alongside the technology, threat intelligence also plays a part. Knowing how to think like criminals and scammers helps to design better defences.
Some of the areas where casinos have improved security:
- Investing in advanced facial recognition and tracking technology
- Adopting threat intelligence training to help staff identify suspicious behaviour
- Analysing how the casino cheats think to develop ways to catch them
Despite the amount spent on security, casinos make attractive targets and mistakes do happen.
Mostyn talked about a few high-profile hacks affecting casinos that made the news headlines, including the smart thermometer on a casino lobby tropical fish tank that was left unsecured on the network.
The lesson for MSPs is to make sure you’re aware of any smart devices your customers use and take steps to secure them. You can segregate them onto their own network, keep them patched and up-to-date, and practice management, including using multi-factor authentication (MFA).
MSPs Are Becoming a More Attractive Target for Hackers
The supply chain of an MSP can be another way for hackers to infect multiple businesses.
As an MSP, your intellectual property (IP) is your access to your customers, and that’s what makes you attractive to hacker groups.
According to a survey by CompTIA, 62% of MSPs are very concerned about being targeted.
The NSA recognises this threat too, and shared some advice for how to make MSP defences more robust:
- Never share credentials between different users. Supply unique accounts with least privilege access to limit exposure if compromised.
- Use two-factor authentication to protect every account, both admin and user, against unauthorised remote access.
- Don’t rely on antivirus software alone to detect a breach. Consider more proactive security, like conducting internal phishing simulations to assess risk and educate users.
- Invest in endpoint security to see how users’ devices are accessing the network and where from.
- Protect against exploit kits leveraging known vulnerabilities. Use endpoint security to create policies that block access from risky devices attempting to gain egress into your network and systems.
The Joint Cyber Security Advisory is an initiative between the UK and the US to tackle cyber crime and share advice on trends and attack vectors.
The Cybersecurity Masterclass Approach to Risk
Interaction was actively encouraged throughout the day. And none more-so than in the session before the lunchtime break.
We were split into four teams and encouraged to engage in discussion before giving our answer to a number of risk-related questions.
I don’t want to give away what we talked about, but it certainly got everyone thinking and talking about risk in general.
It was a great way to round off the morning and keep everyone engaged.
The Cybersecurity Cloudscape
The afternoon of the Cybersecurity Masterclass began with a look at ways (with product examples) of improving your cloud security stack.
Asset Discovery and Compliance
You can’t manage what you can’t see. Furthermore, you can’t prove compliance if you don’t know what’s on your network.
When you have an agreement in place with a customer, it’s important to be clear about what that agreement covers. If that customer has compliance obligations, you need to be aware of that to ensure your solution is adequate.
ConnectSecure is a tool that carries out both security assessment and vulnerability management to ensure assets are secure and risks are mitigated.
Locking Down Your Network
Some of the ways you can secure your network include:
- VPN
- Firewall
- Identity Management
- Conditional Access
- Secure Access Service Edge (SASE)
- Zero Trust Network Access (ZTNA)
- LAN Zero Trust (LZT)
Todyl is a solution that covers most of these bases, and is a great addition to your depth of defence arsenal.
The Weakest Link
People are often the weakest link in your defences.
- 88% of all data breaches are caused by an employee mistake
- 93% of modern breaches involve a phishing attack
- 22% of data breaches involve phishing attacks*
*common phishing attacks involve Loaders, Spear Phishing, Zombie Phishing or URL shortening
However, when staff are trained to spot phishing attacks they become your human intrusion detection system.
Ironscales and Proofpoint are two examples of security awareness training (SAT) tools.
The aim of these tools is to provide training and assessments to change employee behaviour, and can run phishing simulations to put this training into practice.
The Essentials of Cybersecurity
The essentials of cybersecurity for come under three pillars:
Risk Assessment – A record of all company assets with risk ratings and who’s responsible
Vulnerability Assessment – Hire a third party IT professional to conduct a vulnerability assessment and then document them as areas of weakness
Security Monitoring – Train people to be better at noticing suspicious activity and use technical auditing systems to identify unauthorised or malicious activity.
Together, all three will help you identify new risks, as well as what to test and what to monitor.
The vulnerability assessment will determine the risks, and educate staff about the types of threats to expect. In turn, this determines the skills your staff will need to provide effective monitoring.
Compliance and Frameworks
The role of frameworks is to show your customers and regulators that you have taken “appropriate measures” to keep systems and data safe and secure.
The UK Cyber Essentials scheme is a self-assessment questionnaire focused on 5 key security controls:
- Boundary Firewalls and Internet Gateways
- Secure Configuration
- Security Update Management
- Malware Protection
- Access Control
Some of the questions do consider the training of staff, as well as the risks posed by your supply chain.
The Government wants every organisation in the UK to be Cyber Essentials Certified.
It’s worth noting that insurance companies believe that companies with CE in place are 80% less likely to claim on cyber insurance than those without.
Cyber Essentials Plus goes further to include an audit, as well as more in-depth checks of user credentials, 2FA, mobile devices, malware checks, vulnerability scans and an audit of your self-assessment questionnaire.
Cybersecurity Masterclass: Assured Service Providers
Ian Groves of Midlands-based MSP Start Tech gave us an insight into his Microsoft365 solution, and the benefits of becoming an accredited Assured Service Provider.
Start Tech provide Microsoft 365 Business Premium managed services to their customers under three packages. One of these is the core offering, which includes RMM, EDR, backup, teams and email security, security awareness training and signature management.
Then there are two optional add-on packages, one aimed at compliance, and the other aimed at additional security.
Part of the compliance pack includes Cyber Essentials, which is baked-in to the cost. Paying upfront gives customers something to work towards.
Assured Service Providers
The Assured Service Provider initiative was launched in April 2023 by the National Cyber Security Centre (NCSC).
Once you become an Assured Service Provider, you are officially recognised by the NCSC as an official NCSC Cyber Advisor.
In order to become an Assured Service Provider you need to have:
- Cyber Essentials and Cyber Essentials Plus
- And either ISO27001 or IASME Cyber Assurance Level One and Level Two
As well as these, someone from your organisation needs to complete the Cyber Advisor assessment.
Ian said that although it was a big investment, it has provided over £20k in revenue for security audits. It’s also raised the profile of his business dramatically.
There are around 85 Assured Service Providers so far, and not all of them are MSPs.
Cybersecurity Masterclass: Conclusion
The Cybersecurity Masterclass is just one of many different types of events that Pax8 hold for their MSP partners.
As technology providers and business owners, we should all be taking cyber crime seriously. It’s consistently on the rise, and the frequency and sophistication of cyber attacks means that anyone and everyone could be a target.
An event like this shows how much Pax8 invests in building relationships with their partners so that they can get the best out of their security offering.
They are a great chance for MSPs to network with other MSPs too, to discuss what products work for them, and what doesn’t.
Are you a Pax8 partner, and does the Cybersecurity Masterclass appeal to you? Or are you thinking about becoming a partner and want to know what other events they provide? If so, please let us know in the comments.
Pax8 and Cybersecurity Masterclass Resources
The benefits of the Cybersecurity Masterclass don’t end there either!
After the event, attendees are invited to join the Cybersecurity Masterclass Slack channel, where they can get a copy of the event slides and interact with other members of the community.
Anyone in the channel can ask their questions, share content and ideas and talk about what tools work for them and what doesn’t.
You can find out more about Pax8 UK’s upcoming events here.















Comments