You may be aware that Huntress have recently published their Cyber Threat Report 2025, and it makes for interesting reading. Based on data gathered over the last 12 months, the cybersecurity experts have produced a valuable analysis of the threats managed service providers (MSPs) and IT professionals need to know about.
What’s Included in the Huntress Cyber Threat Report?
The report starts with a detailed examination of the 2024 threat landscape, followed by a look at the risks to specific industries:
• Healthcare
• Technology
• Education
• Government
• Manufacturing
Then, there is a breakdown of specific threat types:
• Ransomware
• Attacker tools and techniques
• Exploit-driven campaigns
• MITRE and ATT&CK phases
• Phishing
• Identity threats
And a breakdown of hacker activity, looking specifically at timeframes. The report itself is almost 80 pages long, and definitely worth getting yourself a copy. Here, we share a few key highlights to give you an idea of what’s included and what to be aware of.
Key Highlights to Know
1. There has been a proliferation in what are known as RATs – remote access trojans. These are multi-stage backdoor with advanced capabilities. Worryingly, Huntress says: “As the malware market gets more competitive, the developers of RATs will add more complex features.
2. Remote monitoring and management (RMM) tools are increasingly targeted by malware. By gaining access through a tool and blending in, the hackers are able to be persistent with their attacks.
3. Ransomware strategies, perhaps not surprisingly, are also changing. Cybercriminals are moving away from encryption to concentrate more on data theft and extortion.
4. We’re also introduced to the concept of ‘living off the land techniques’. These are highly sophisticated and involve focusing on admin tools such as LOLBins and Sysinternal Suite.
5. Finally, phishing techniques continue to evolve and become ever more sophisticated. QR codes, brand impersonation and image-based content were all issues in 2024.
Ransomware
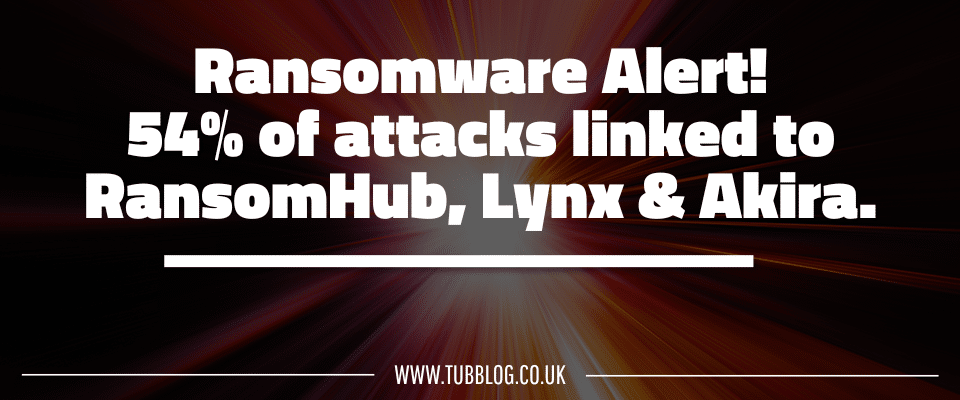
In the past two years, there have been several significant ransomware attacks, targeting companies around the globe. Huntress reports that 54% of ransomware attacks were linked to RansomHub, Lynx and Akira.
The report goes on to highlight the differences in how ransomware groups conducted their attacks. “Time-to-ransom (TTR) analysis revealed that groups like Akira deployed ransomware within six hours of initial access, favouring quick, high-impact attacks.”
Others were slower, and “the number of malicious actions before ransomware deployment also varied, with extortion-focused groups performing more extensive reconnaissance, privilege escalation, and data exfiltration compared to groups prioritising rapid encryption.”
Ransomware criminals operate in groups, and while law enforcement have been successful in disbanding some, the members simply move to a new home. One group that Huntress highlights MSPs beware of is BlackSuit (aka Royal).
This group aggressively targeted business workforces throughout the world in 2024. They’re growing, so MSPs can expect to likely see more sophisticated attacks and methods coming from them.
Identity Threats
Microsoft 365 environments were attacked more frequently in 2024, and these attacks were also more sophisticated. While Huntress have introduced attacker-in-the middle (AitM) detection, MSPs need to beware of the dangers.
Criminals used plugins, tools, unauthorised geolocations and restricted VPNs to attempt to compromise cloud structure. The increase in cloud attacks is almost certainly due to the increasing numbers of organisations using the cloud.
Of the eight categories of identity threat highlighted by Huntress, the two biggest were VPN rule violation and inbox rule modification. The first of these is where the cybercriminal abuses the VPN to “conceal their real IP address or try to bypass geolocation fencing rules to access data.”
And the second requires the attacker to access M365 accounts to use modified inbox rules to siphon off email information. Mostly this was done by moving content to the RSS feeds folder or the conversation history folder. Sometimes they’d even mark emails as ‘read’ to fool the user.
Phishing
Huntress are able to find out almost in real time about potential email threats by speaking to students taking part in their Security Awareness Training (SAT). This not only enabled them to identify the typical attack methods, but to see how many types there are (285 distinct groups).
The report highlights eight notable phishing themes from 2024, with the two biggest being e-signature impersonation and image-based content. It also shows that fake thread/reply chains are becoming more common.
We learn that e-signature impersonation isn’t about your email signature, but about digital requests for your signature, via tools such as Docusign or Adobe. There are two methods for malicious acts here.
The first is by creating ‘fake graphical emails that look as if they’re from the e-signature provider.’ The second, more sophisticated approach is using the provider itself to host either a malicious document or document linked to a malicious site.
And image-based content attacks are cleverly designed to “bypass text-based spam filters and send an image which is hyperlinked to a malicious landing page. The image in its entirety is linked, and is the only element in the email,” which explains why the recipient ends up clicking.
What do you think? Have you got a copy of the report? What have you observed in your own MSP in the last 12 months and what’s a priority for your clients? Let us know in the comments.















Comments