Why use a strong password?
We’re all used to being told how important it is to use a strong password, but unfortunately, it tends to be one of those things that unless it happens to us, we don’t take it seriously.
At a guess, if your home was broken into then you probably wouldn’t shrug your shoulders and say it was “one of those things”. Even if nothing of value was taken, you’d probably still feel disturbed that somebody had gained unauthorised access to your property and belongings.
How would you feel if the same thing happened and somebody gained unauthorised access to your company computer systems?
![]()
What happens if you don’t have a strong password?
We recently helped a client migrate their systems from a peer to peer network to a Windows Small Business Server 2008 (SBS 2008) network with central file storage, e-mail and strong security.
In the previous peer to peer network, the security was very minimal. Users had passwords, but they never changed… ever. Passwords were often the same as the user-names, or were very simple – cat, dog, that sort of thing. Files were shared amongst everyone in the system without any permission structure in place.
In effect, anyone who had access to the network had access to ALL the network – including anyone who could guess a user-name and password!
SBS 2008 takes security seriously, and after implementing the new network infrastructure we talked to the client about the new strong password policy they would have in place. The client had lots of questions, many objections to the new way of working (“But we’ve always done it this way”, “I don’t see the point”, “People won’t remember all that”) and generally a resistance to change. This is human nature – change is difficult, but people are adaptable.
So what is the difference between a strong password policy, and a weak password system?

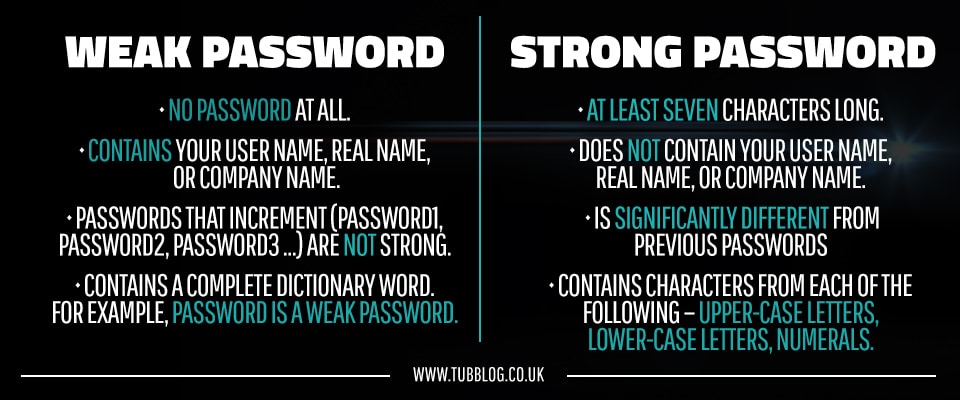
What is a weak password?
A weak password provides attackers with very easy access to your computer system.
Password-cracking software continues to improve, and the computers that are used to crack passwords are growing more powerful than ever. Password-cracking software generally uses one of three different approaches: intelligent guessing, dictionary attacks, and brute-force automated attacks that try every possible combination of characters.
A weak password:
- Is no password at all
- Contains your user name, real name, or company name
- Contains a complete dictionary word. For example, Password is a weak password
What is a strong password?
Strong passwords are considerably harder to crack (or break) – and that’s even with the powerful password-cracking software that is available today. Given enough time, the automated method can crack any password.

However, strong passwords are much much harder to crack than weak passwords. A secure computer system has strong passwords for all user accounts.
A strong password:
- Is at least seven characters long
- Does not contain your user name, real name, or company name
- Does not contain a complete dictionary word
- Is significantly different from previous passwords. Passwords that increment (Password1, Password2, Password3 …) are not strong
- Contains characters from each of the following four groups – upper-case letters, lower-case letters, numerals
A computer system or network should have a mandatory password policy put in place. This policy will dictate that passwords must be strong, meeting the above criteria, and also be changed after a set period of time – say, 42 days.
Do I really need a strong password policy straight away?
Rephrase this question… as yourself, “Should I adopt a strong password policy now…. or after an unauthorised user has gained access to my files?”
This isn’t scaremongering and it’s not a case of if, it’s a case of when. We regularly see random hacker attacks on all our client systems – even those with security in place.
Generally these are random attacks probing for weaknesses. Think about it in terms of household security. Which houses do burglars target, those without signs of security, or those with windows and doors left open?
The same is true of of computer security. By adopting strong security policies, you don’t eliminate the risk of attack, but you do become a less attractive target.
Couldn’t we all just use the same password?
Yes, it would make it easy for everyone to log on.
But that everyone might include the cleaner, the security guard, Mary in Finance, hackers trying to access the network from the Internet, an employee checking out his appraisal compared to his colleagues, a disgruntled staff member looking to destroy some data, or worse, your competitor who has gained access to your network.
By having individual strong passwords for each user, you’re drastically reducing the risk of these scenarios, or similar, ever occurring.
Can I write strong passwords down?
I often get asked if strong passwords can be written down so that managers and the HR department can access to everybody’s files and emails.
If a member of staff writes his password down on a post-it note in his desk drawer, or worse, attaches it to his monitor, then that password isn’t secure at all – the whole system is vulnerable.
You could get every member of staff to write their password down on a piece of paper kept centrally, say with HR or the boss, but as passwords are best changed every 30-40 days, this will turn into a laborious exercise in administration very quickly.
A better solution would be to simply dynamically give the boss or HR department access to those files or emails they need to from their own logon and computer as and when needed, or less preferably but if necessary, give them permanent access to all those resources from their own logon and computer.
Can we ask the IT department to tell us other people’s passwords?
The IT department don’t have access to users existing passwords, they can only reset these passwords to something new. This creates an audit trail of who changed a password and when.
When Joe is on holiday or off-sick, Dan needs access to their files and email – if Dan hasn’t got Joe’s password to log on to his computer, how can he cover his work?
Rather than sharing passwords and logging on to a computer as Joe, Dan can be given access to Joe’s e-mails and files from his own computer and logon. This could be temporary, so when Joe returns from his absence Dan no longer has access to his files or e-mails.
![]()
Can folders be password protected?
If you’re following the advice we’ve given previously, with every user having their own logon and password, then any file folder can have very granular security, allowing or denying a single user or group of users access to those files or sub-folders.
For instance, you may have a Public Folder containing four folders – Staff Information, Design Drawings, Accounts and HR. Everybody in the company needs access to Staff Information. Everybody needs access to Design Drawings, but only the Design Staff should be able to modify or delete files within that folder.
Only the Finance Department and the boss need access to the Accounts folders, and only the HR department need access to the HR folder.
It’s very simple to set-up granular permissions for this scenario, provided everybody has their own user-name and password.
![]()
Conclusion
If you haven’t got a strong password policy – then why not? Be honest with yourself – are you ignoring that advice from the Police and leaving the windows and doors to your home wide open? Or are you being realistic, realising that threats do exist and mitigating this risk by taking reasonable steps?
Thoughts and your own computer security advice welcome! If I can offer any advice or point you in the direction of an IT company who can help you with your own requirements, don’t hesitate to get in touch!
![]()











Comments
8 thoughts on Why use a strong password?
CHRIS
24TH FEBRUARY 2010 08:43:15
Ric... Once again, brilliant blog post from the TUBBMASTER ... I have been talking with a customer about the very same thing, and so I may use some of your stuff in the document that I give to them.,
RICHARD
28TH FEBRUARY 2010 09:44:00
Chris - thanks for the feedback, feel free to SWIPE away for use with your own clients. :-)
RAGAIUS
26TH OCTOBER 2011 04:50:43
I know it has been almost 2 years since the last post regarding this excellent article but my employers have been questioning the need for strong passwords and this site came up in my research. Since the Windows administrator password on a stolen laptop can be reset with easily obtainable tools, why should they bother to use a strong password? This is the question I'm getting. The argument I am making is that weak passwords are easily stolen by guesswork or shoulder attacks from a malicious user who may not be able to steal the machine, thus gaining access in an unguarded moment. Combined with reasonable user precautions like locking their machines and being aware of who is around when typing a password, strong passwords make it much more difficult to get compromised. Was wondering if I'm missing any other good arguments?
TUBBLOG
26TH OCTOBER 2011 07:40:18
Thanks for the kind words - I'm glad you found the article useful! In terms of laptops, I'd argue that using some form of encryption for data and/or laptop security software would always be wise. That said, unless the laptop is targeted and stolen specifically for its data (and most I'd say are stolen purely for the hardware) then a strong password would deter most typical thieves from trying to get at the data on the hardware. Your employers argument about not bothering to use a strong password because it's possible to crack them is akin to saying they also won't bother with a security alarm on the office because an experienced burglar could disable the system. Just my $0.02 :-)
RAGAIUS
26TH OCTOBER 2011 14:31:50
Richard: Much thanks for the quick reply! I can use that argument :) We are implementing whole disk encryption and the users are somewhat disgruntled that they will have to remember a strong disk password AND a Windows password. They are hoping for a free pass on an easy Windows password. Not going to happen. In spite of this I am starting to feel that strong passwords are becoming obsolete in the sense that in order to provide real protection they should be at least 20 characters. Most end users can't be made to do that reliably.
TUBBLOG
26TH OCTOBER 2011 18:24:32
Another option to consider is Two-Factor Authentication. A password and a qualifying code from a token is a very secure method. Many "tokens" nowadays can be apps running on iPhone and Android too.
JUBAIR
16TH JULY 2019 06:02:57
Thank you so much for your lovely article. I have learnt so many things about strong password. This is really a helpful article.
RICHARD TUBB
25TH JULY 2019 10:25:01
Thank you, Jubair!